Windows Command Prompt (CMD. EXE) is a shell program under Windows NT to run Windows control panel programs or some DOS programs, or under Windows CE only to run control panel programs. CMD instructions have a lot of use is also very wide!
Here are some more advanced instructions for those of you who have some basic knowledge of computers or have studied them in greater depth.
Such as disk, directory, File Operation Code. Disk, fdisk implied, parameter/MBR rebuilds master boot record fdisk/MBR rebuilds master boot record
After DOS7.0, fdisk added the/CMBR parameter to rebuild the master boot record of the underlying hard disk when mounting multiple physical hard disks, such as fdisk/CMBR 2, which overrides the master boot record of the second hard disk. Be very careful when using it to avoid damaging the good hard disk boot record
Format parameter:/Q Quick Format/U unrecoverable/autotest not prompted/S create MS-DOS boot disk format C:/Q/u/autotest
Table of contents,
[/s ][/w ][/p ][/a ] lists directories, parameters:/s looks for subdirectories/W only shows file name/P page/a shows hidden file formatdir. EXE/s finds the format of the disk. EXE file and report the location
MD (Mkdir)-LSB- directory name ] create directMkdirKHelloworldORLD creHelloworldODirectorytory
CD (Chdir)[ directory name ] PS: you can use a relative or absolute directory to go to the Directory CD AA to go to the AA directory under the current folder, CD:. Go to the previous folder CD returns to the root directory; CD C: Windows goes to the C: Windows Folder
RD (RMDIR)[ Directory name ] delete directory RD Helloworld Delete Helloworld Directory
Documents,
delete directory and its files: RMDIR [ directory name or file name ][/s ][/w ][/p ][/a ]. Example RMDIR C: qqdownloads delete the QQDOWNLOAD Directory of the C disk.
Del [ directory name or file name ][/F ][/s ][/Q ] delete, parameter:/F delete read-only file/S delete the directory and all contents under it/Q delete before confirmation
Del C: Del/s/Q automatically deletes the DEL directory of the C drive.
Copy -LSB- source or directoryDestinationtDirectorytorCopycDpyPWIN98in98 * . * C: presetup copies all PWIN98 files from Disk D to Disk C under presetup.
Attribub [ parameter ][ source or directory ] file properties Operation Command, attribub command can list or modify the properties of a file on disk, including document (a) , read-only (R) , hidden (h) , system (S) , such as: b-h-r-s io. When SYS executes this command, it will send the DOS system file IO. SYS file read-only, hidden, system properties removed, this will be directly through the DIR command to see Io. SYS file. This is an application that can be applied to an application like this. Bat adds the above attributes to an automatic batch file.
And other operations.
NET use IPIPIPC $user creates an IPC empty link
NET use IPIPIPC $password user name, establish a non-null IPC link
Net use H IPC $password user name, direct login mapping the other C: to the local H
Net use H IPC Login and map the other C: to the local H
NET use IPIPIPIPC $del delete IPC Link
NET use H del deletes the mapping of the other party to the local mapping of H
NET user username, password add creates the user
NET user guest activeyes activates the guest user
NET user to see which users there are
NET user account name, see the properties of the account
Net localgroup administrators username add adds “User”to the administrator to give it administrator privileges. Note: Administrator followed by s in the plural
NET start looks at which services are enabled
NET start service name, opening service; (for example, net start telnet, net start schedule)
NET stop service name, stop a service
NET time target IP to view each other’s time
NET time target IP set sets the time of the local computer to be synchronized with the time of the “Target IP”host, with the parameter yes to cancel the confirmation
Net view to see which shares are enabled within the local LAN
Net View IP to see which shares are enabled on the other side’s LAN
NET config shows system network settings
NET logoff disconnected sharing
NET pause service name to suspend a service
NET send IP text message to the other party
Net Ver the type of network connection and information being used within the LAN
NET share to view locally enabled shares
NET share IPC $turns on the IPC $share
NET share IPC $del delete IPC $share
NET share c $del Delete C: SHARE
The net user guest 12345 uses the guest user to log in and change the password to a 12345
NET password, change the system login password
Netstat-a to see which ports are turned on, often using netstat-an
Netstat-n looks at the network connectivity of the port, often using netstat-an
Netstat-v to see what’s going on
Netstat-p protocol name example: netstat-p TCQIP to see how a protocol is being used (to see how TCPIP is being used)
NETSTAT-S looks at all the protocol usage in use
Nbtstat-a IP. If one of the ports 136 to 139 is open, you can check the last user name (before 03)-note: parameter-a is capitalized
Tracert-parameter IP (or computer name) traces the route (packet) , parameter:”-W number”to set the timeout interval.
Ping Ip (or domain name) sends a default size of 32 bytes to the other host. Parameters:”-L [ space ] packet size”;”-N number of times the data is sent”;”-t”means always ping.
Ping-t-l 65550ip Death Ping (sending files larger than 64K and pinging all the time becomes Death Ping)
Ipconfig (winipcfg) is used for Windows NT and XP (Windows 9598) to view local IP addresses, and the ipconfig parameter “All”shows all configuration information
TLIST-T displays the process in a tree row list (as an add-on to the system, not installed by default, in the Supporttools folder in the installation directory)
KILL-F process name plus-f parameter to force a process to end (for system add-on tools, the default is not installed, in the Supporttools folder in the installation directory)
Del-f file name plus-f parameters can delete read-only files, AR, AH, AS, AA, respectively, that delete read-only, hidden, system, archive files, a-R, A-H, A-S, A-A mean deleting files other than read-only, hidden, system, and archived. For example, “DELAR.”Means delete all read-only files in the current directory, and “DELA-S.”Means delete all files in the current directory except system files
Del S Q directory, or delete the Directory and all subdirectories and files under the directory with: RMDIR S Q Directory S. At the same time, parameter Q can be used to cancel the deletion operation when the system is confirmed to delete directly. (the two commands are the same)
Move Drive Path to move the file name, move the file name, move the file name, move the file, with the parameter Y will cancel confirmation move directory exists the same file prompt on the direct overwrite
FC One. TXT two. . . TXT 33st. TXT compares the two files and prints out the differences to 3ST. TXT file, and is the redirection command
The at ID number opens a registered scheduled task
At delete stops all scheduled tasks, and with the parameter yes it stops without confirmation
The at ID delete stops a registered scheduled task
The at looks at all the scheduled tasks
A T I P time program name (or a command) R runs the other program at a certain time and restarts the computer
Finger username@host to see which users have logged in recently
Telnet IP port, remote and login server, default port 23
Open IP connects to IP (which is a command after telnet login)
Typing Telnet directly on the local machine will access the native telnet
Copy path file name 1 path file name 2Y copy file 1 to the specified directory as file 2, with the parameter y cancel confirmation you want to rewrite an existing directory file
Copy CSR V. EXE ipad min $copy local CSR V. EXE to the other admin
Cppy 1 ST. JPGB + 2st. Txta 3 ST. JPG will be 2st. TXT’s content is hidden in 1st. Generate 3st. JPG. New JPG file, note: 2st. TXT file header to empty three rows, parameters: B refers to the binary file, a refers to the ASCLL format file
Copy ipad min $svv. Exe C or copyipadmin $. Copy each other’s admini $shared SRV. EXE files (all files) to local C:
Xcopy to copy the file or directory tree, Destination Directory name, copy the file and directory tree, with the parameter y will not prompt to overwrite the same file
TFTP-I own IP (meat machine as a springboard for this meat machine IP) get server. , . EXE cserver. Exe login, “IP”will be the server. EXE to the target host cserver. exe. EXE parameter:-I refers to the binary mode of transmission, such as when the transmission of EXE files, such as without-i in ASCII mode (transmission text file mode) for transmission
Tftp-i IP put server. EXE login, upload local cserver. exe. EXE to host
FTP IP port for uploading files to the server or performing file operations. The default port is 21. Bin refers to the binary mode of transmission (executable file into) ; the default format for ASCII transmission (text files)
Route print displays the IP route and will primarily display Network addresses, subnet mask Netmask, Gateway addresses, and Interface addresses
ARP views and processes the ARP cache, which is the name resolution that resolves an IP to a physical MAC address. Arp-a will display all the information
Start program name or command max or Min to open a new window and maximize (minimize) to run a program or command
MEM to see the CPU usage
The file name (directory name) at the attribute of a file (directory)
The file name-a-r-s-h or + A + R + S + H removes, archives, read-only, system, hides, or attributes from a file; + is added as an attribute
Dir view files, parameters: Q show the file and directory system which user, TC show file creation time, TA show the last time files were visited, TW last modified time
Date T and time t use this parameter, “DATET”and “Timet,”to display only the current date and time without entering a new date and time
Set specifies the name of the environment variable = the character to assign to the variable and sets the environment variable
Set displays all the current environment variables
Set P (or other characters) displays all environment variables that currently begin with the character P (or other characters)
Pause pause the batch program and display: press any key to continue...
If performs conditional processing in a batch program (see if commands and variables for more information)
The Goto label Will CMD. EXE to the labeled line in the batch program (the label must be a single line, beginning with a colon, for example:”: Start”label)
The name of the call path batch file from which another batch program is called (see call for more information)
For executes a specific command for each file in a set of files (see for commands and variables for more information)
Echo on or off turns echo on or off, and the current echo setting is displayed with Echo alone and no arguments
Echo message, displays the message on the screen
Echo message passed. TXT saves the information to pass.txt. TXT file
Findstr Hello A. TXT in A. Find string hello in the. TXT file
Find the name of a file
Title title name, change the CMD window title name
Color color value, set the background and background color of the CMD console; 0 = Black, 1 = blue, 2 = Green, 3 = Light Green, 4 = Red, 5 = purple, 6 = yellow, 7 = White, 8 = gray, 9 = light blue, A = light green, b = Light Green, C = Light Red, D = Lavender, E = light yellow, F = Bright White
Prompt name, Change CMD. EXE display of the Command Prompt (C, D unified changed to: Entsky)
VER displays version information under the DOS window
Winver popup a window showing version information (memory size, system version, patch version, computer name)
Format disk type FS, formatted disk, type FAT , FAT32, NTFS, for example: Format D FSNTFS
MD directory name, Create Directory
Replace source file, to replace the Directory of the file, replace the file
Ren original file name, new file name, rename file name
The tree displays the directory in a tree structure, and with the parameter-f, the name of the file in the th folder is listed
Type file name that displays the contents of the text file
The name of the file, which displays the output file screen by screen
Doskey to lock command = character
Doskey to unlock command = the lock command supplied for DOS (edit the command line, re-invoke the WIN2K command, and create the macro). For example: Lock Dir Command: Doskey Dir = Entsky (can not use doskey = dir) ; unlock: Doskey Dir =
Taskmgr pull up task manager
CHKDSK FD checks Disk D and displays status reports; takes parameter F and fixes errors on the disk
You can change the Telnet service default port 23 to any other port by typing TLNTADMN Select 3 and then Select 8
Exit exits CMD. EXE or currently, exit the current batch script with parameter B instead of CMD. Exe
The file name of the path path executable, setting a path for the executable.
CMD launches a win2K command interpretation window. Parameters: EFF, En off, open command extension; see CMD for more details
Regedit s registry file name, import the registry, parameter s refers to quiet mode import, without any hint;
Regedit E registry file name, Export Registry
Cacls file name, parameters, display or modify file access control list (ACL) -- for NTFS format. Parameters: D user name set to deny access to a user; P user name Perm to replace the access rights of the specified user; G user name Perm to give access rights to the specified user; Perm can be n no, R read, W write, C change (write) , F complete control; Example: Cacls D Est. . TXT D pub set D Est. . Pub User Access. TXT denied.
Cacls file name to see the list of access user permissions for the file
REM text content, annotated in a batch file
Netsh to view or change the local network configuration
Wait for the command.
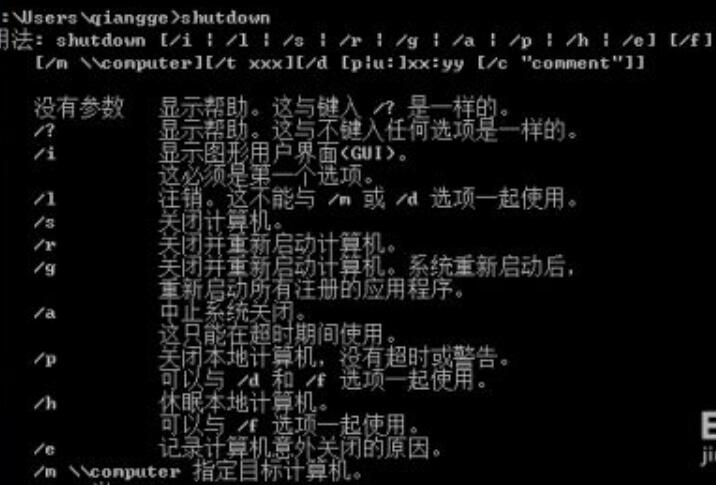
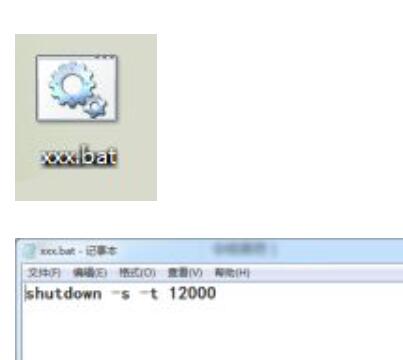
We can take a CMD command shutdown to demonstrate it. Open CMD, type shutdown. If you want shutdown to type shutdown-s, restart shutdown-r to shut down, you can type shutdown-s-t XXX. XXX means how many seconds to shut down for a minute and 60 seconds, and then you can type shutdown-s-t 60, depending on the situation. If you do not bother to open the CMD input instructions can be made a XXX. BAT file. Method: Open Notepad input shutdown or restart the timing shutdown (depending on the user) code, SAVE, file name can edit itself but the suffix name must be changed to bat file.
CMD instructions for certain people have a lot of use, must not be used for illegal purposes.



 Account not verified
Account not verified